Hi there, hope this finds you fine.
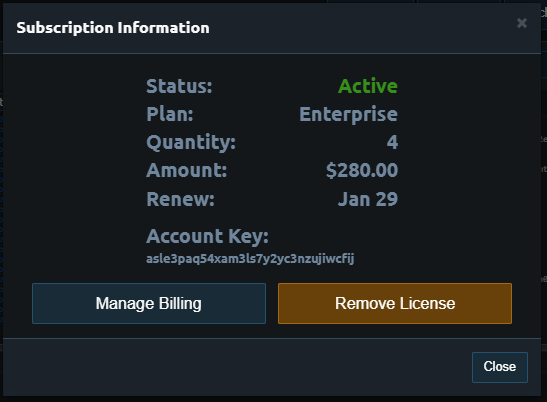
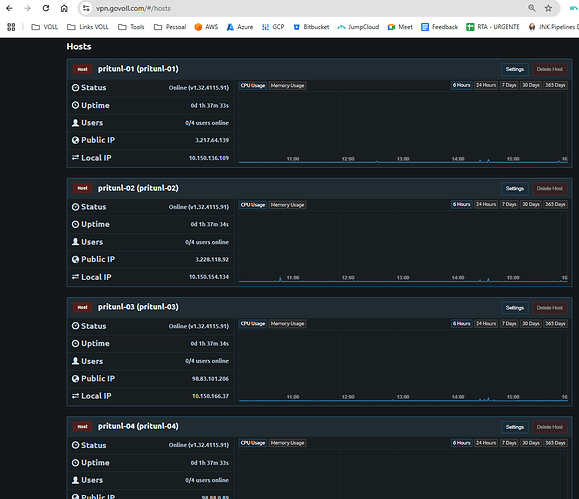
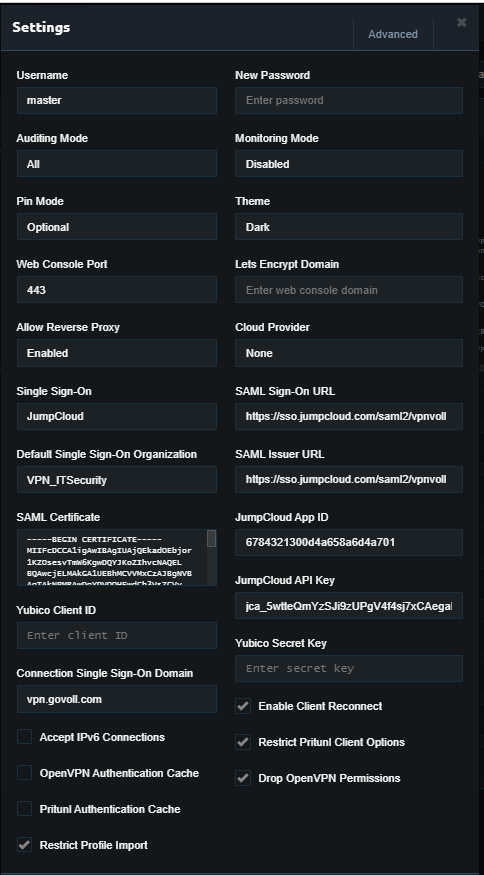
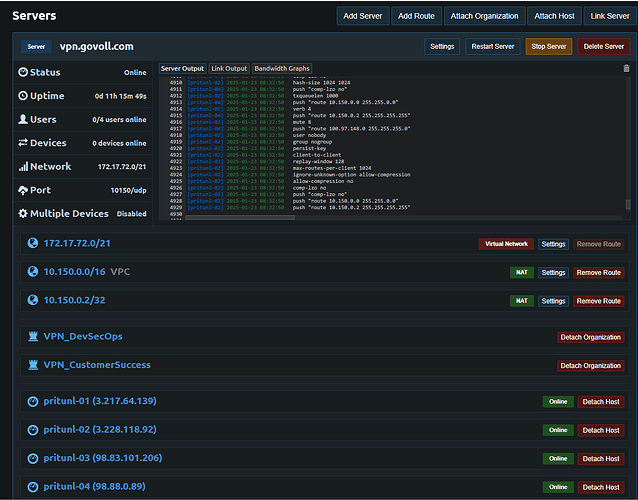
Recently we purchased 4 Pritunl Enterprise licenses to accomplish a high availability VPN. We have 4 Pritunl VPN Servers (hostnames: pritunl-01,pritunl-02, pritunl-03, pritunl-04) on AWS in the same region, every one in AZ (a,b,c,d) and one with Mongodb (AZ C, hostname: mongodb). We also configured SSO with Jump Cloud enabling device authentication.
In this AWS Account we configured a private DNS (interno.govoll.com), a NLB (internet facing, 4 zones and 4 public IPs), 2 ALBs (both private, 4 zones and 4 private IPs each).
VPC CIDR: 10.150.0.0/16
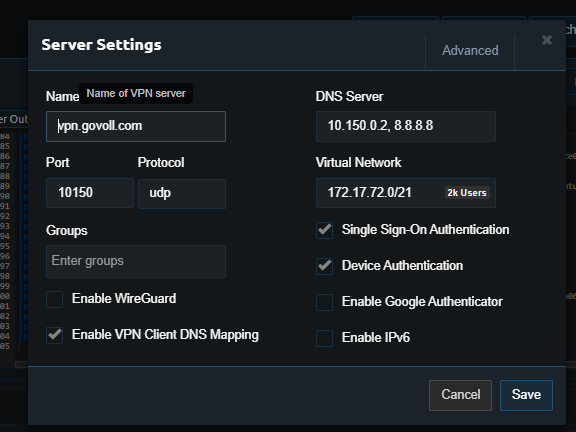
Pritunl Virtual Network: 172.17.72.0/21
PRIVATE DNS: interno.govoll.com
PUBLIC DNS: vpn.govoll.com
The flow to connect in this VPN are:
{INTERNET} → [NLB: https and udp 10150]
[NLB UDP 10150] → [TARGET GROUP TO INSTANCES]
[NLB TCP 443] → [ALB-1 HTTPS] → [TARGET GROUP PROXY SERVERS - nginx ] → [ALB-2 HTTPS] → [TARGET GROUP WITH THE 4 PRITUNL SERVERS]
- The NLB security group allows UDP 10150 and HTTPs from anywhere, both IPV4 and IPV6.
- The ALB-1 security group allows HTTPs everywhere IPV4 and all traffic from the VPC CIDR (10.150.0.0/16) and VPN Network (172.17.72.0/21)
- The ALB-2 security group allows HTTPs everywhere IPV4 and all traffic from the VPC CIDR (10.150.0.0/16) and VPN Network (172.17.72.0/21)
- The mongodb server allows TCP 27017 from VPC CIDR
- The Pritunl servers allows 10150 from everywhere (IPV4 and IPV6) and 443 IPV4
- The reverse proxy servers allow all traffic from VPC CIDR and Pritunl Virtual Network.
- All servers are configured to search first in interno.govoll.com in the resolv.conf
- The hostname to connect in this VPN is vpn.govoll.com (public dns, type A record with ALIAS to NLB pointed to the NLB).
- Have only one server named vpn.govoll.com.
- We removed 0.0.0.0/0 route and add 10.150.0.0/16 NAT, 10.150.0.2/32 NAT
- We attached 2 organizations from the JumpCloud User Group.
- We attached the 4 Pritunl servers hosts
- We disable the WAF ACL until we resolve the connection issue.
- We are using the latest version of Pritunl Client.
- Softwares versions:
- Ubuntu 24.04.1 LTS (Noble Numbat)
- Linux pritunl-01 6.8.0-1021-aws #23-Ubuntu SMP Mon Dec 9 23:59:34 UTC 2024 x86_64 x86_64 x86_64 GNU/Linux
- pritunl v1.32.4115.91
- Mongodb version v8.0.4
- When the connection works fine, it’s possible to reach and connect to hosts in private DNS normally.
Our problem is: We need to try several times before we can connect on the VPN and I think it is because of the 4 different public IPs in the NLB.
Considerations:
- We need to keep close to this architecture because this will be used for other applications segregated by host header.
- We want to use a reverse proxy layer to inspect request.body for auditing.
What we tried already:
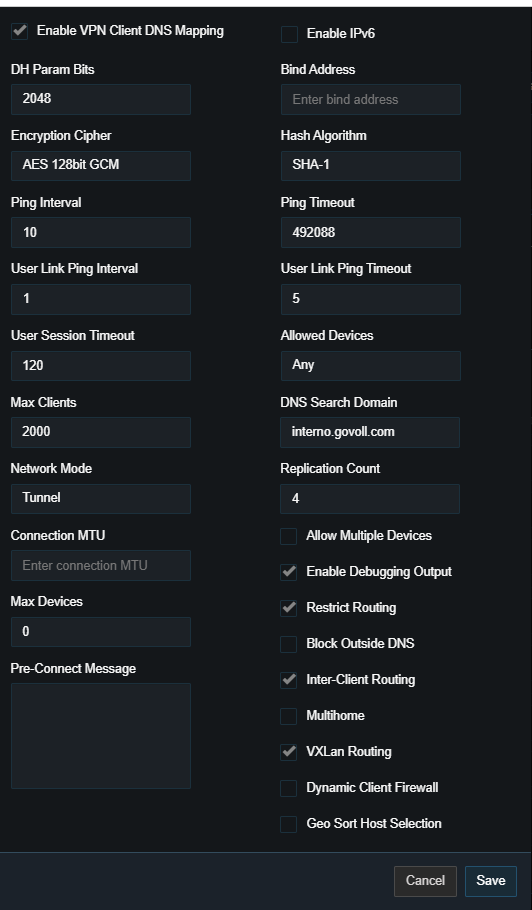
- Enable/Disable VXLan Routing
- On the hosts set the public IP in each AZ to the server in the same AZ in Public Address
- On the hosts set vpn.govoll.com in sync, link and public address
- On the hosts set private IP of the server in Local Address.
- At this moment the 4 hosts are resolving public IPs from natgateway (we stop changing config).
Thank you in advance