Hello,
I’m experiencing an issue with RADIUS authentication in Pritunl when enabling Device Authentication (TPM) on the client side. The issue appears to be related to how the User-Password is encrypted and sent to the RADIUS server (Windows NPS).
What works:
- When Device Authentication is disabled, Pritunl successfully authenticates against the RADIUS server.
- The RADIUS request contains a standard User-Password field, encrypted using the expected method, and authentication succeeds.
What fails:
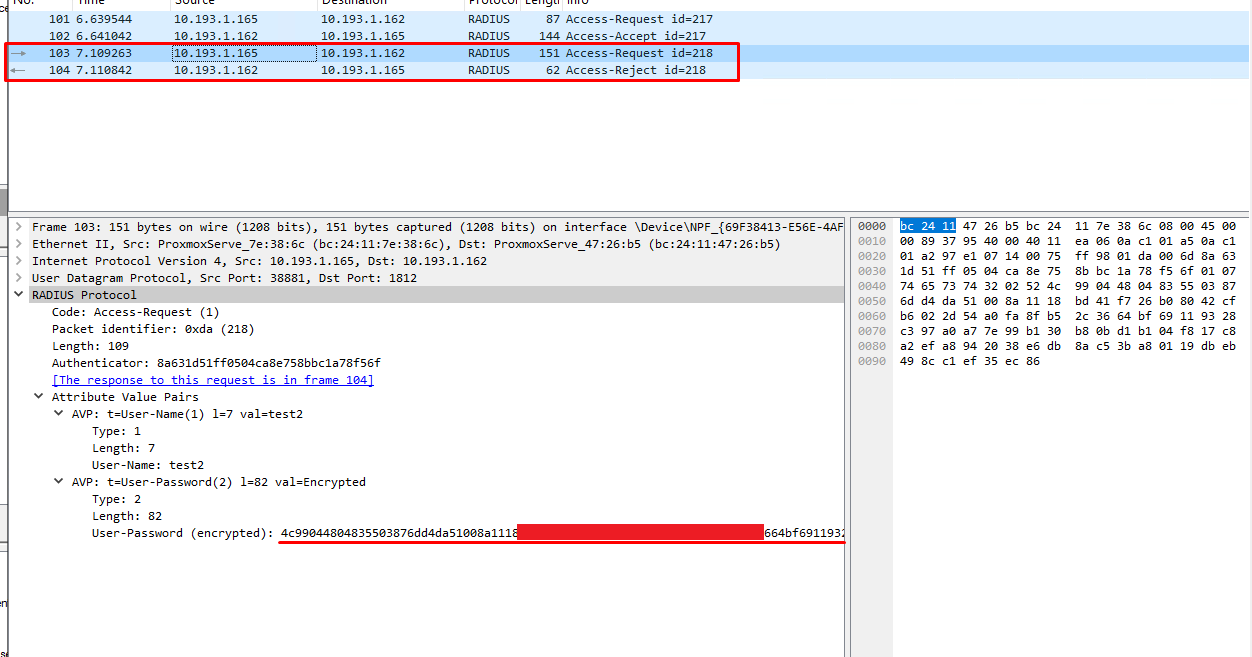
- When Device Authentication (TPM) is enabled, Pritunl sends an additional Access-Request to the RADIUS server.
- The User-Password (encrypted) field in this request is significantly different from the one sent without TPM.
- Windows NPS rejects the authentication with
Access-Reject.
Debugging details:
- I captured and compared the RADIUS requests using Wireshark.
- The only significant difference between a working and a failing request is the length and content of the User-Password field.
- The authentication fails with
Failed secondary authenticationin Pritunl logs.
Possible cause:
It seems that when TPM-based authentication is enabled, the way User-Password is encrypted or hashed changes, causing Windows NPS to reject it.
Since Pritunl’s radius.py uses PwCrypt(password), I suspect that Windows NPS might be expecting a different hashing method (such as MS-CHAPv2 or EAP-TLS) instead of the standard RADIUS MD5-based encryption.
Questions:
- How does Device Authentication (TPM) affect the way Pritunl encrypts or hashes the password before sending it to RADIUS?
- Is there a way to ensure that Pritunl always sends the password in a format that Windows NPS expects?
- Has anyone successfully used Windows NPS with TPM-based authentication in Pritunl?
Any insights or suggestions would be greatly appreciated!
Thanks.