OpenSSL will be releasing a critical security patch on November 1st, 2022. A Pritunl server will have 2-3 services open to the internet assuming other unnecessary services such as SSH are properly controlled with a firewall. Only the OpenVPN process utilizes OpenSSL. No updates will be required for the Pritunl package, the OpenSSL package will need to be updated from the Linux distribution that is running the Pritunl server. Once the OpenSSL package is updated the server should be restarted to load the updated OpenSSL library. Below is a description of the 3 external components of a Pritunl server.
The impact of this OpenSSL vulnerability and any future vulnerabilities with OpenSSL, OpenVPN or WireGuard can be competently prevented by using the recently added dynamic firewall explained below. For security critical deployments of Pritunl it is recommended to proactively enable this before the OpenSSL announcement tomorrow. But doing this will require updating all Pritunl servers and all users to update to the latest Pritunl Client.
Additional information on the security design of Pritunl is available in the security documentation.
Pritunl Server Components
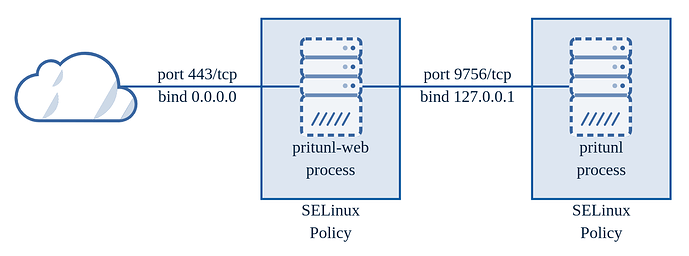
- Pritunl Web Server
The Pritunl web server is a dual server design using an external Golang web server and internal Python web server. The external Golang web server protects the less secure internal Python web server and provides an additional layer of isolation from the core Pritunl process. It also provides full type checking of all the json formatted data coming into Pritunl. This type checking prevents potential injection attacks on MongoDB queries and other attacks inherent in a type unsafe language like Python. HTTP headers are also filtered in the external web server. Additionally every HTTP request is recreated and json data reserialized instead of being copied in the external web server before being sent to the internal web server. This prevents attacks that can arise from incorrect HTTP request parsing on the Python web server. On RHEL based distributions (not including Amazon Linux) the external web server process is further isolated with SELinux policies included in the Pritunl package. All TLS for HTTPS requests is handled by the external Golang web server which utilizes the crypto/tls library. The Pritunl web servers does not utilize OpenSSL.
- OpenVPN Server
The OpenVPN process utilizes OpenSSL and is running as root by default. The process can be configured to drop to a non-root user by enabling Drop OpenVPN Permissions in the top right settings from the web console.
- WireGuard Server
The WireGuard server does not utilize OpenSSL.
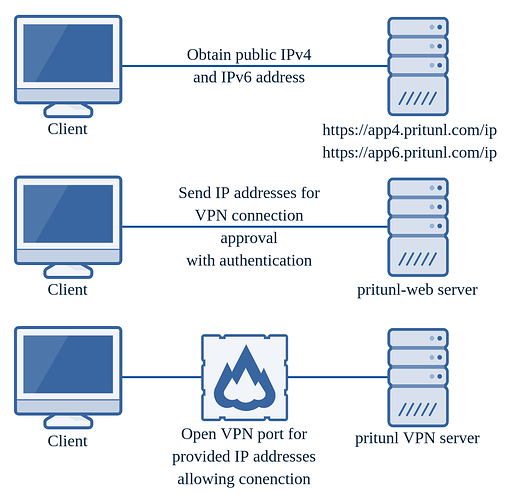
Dynamic Firewall
The dynamic firewall was recently added to Pritunl to provide a VPN server that is almost impossible for an unauthenticated user to exploit. It is available on the newer versions of Pritunl with an enterprise subscription. Once the dynamic firewall is configured only the Pritunl web server will be open to the internet. All VPN server ports will be closed by default. This is a per-server option to allow transitioning a user base from a non-dynamic firewall server to a dynamic firewall server. For a user to connect to a VPN server the Pritunl Client will send an authenticated web request to the Pritunl server requesting to connect to a server. This request will include the users public IP address from three sources, the IPv4 and IPv6 Pritunl public app servers and the client IP address as detected by the Pritunl web server. The Pritunl server will then open the VPN port to those IP addresses for the server the user requested a connection to. Once this is done the Pritunl Client will then open a VPN connection to the Pritunl server. Once the clients connection ends the users IP address will be removed from the VPN firewall. Although any other users sharing a public IP address with the authenticated user will gain access to the VPN server port this still significantly reduces the threat of attacks on the VPN servers. This additional layer of protection along with the multiple layers of hardening on the Pritunl web server will provide one the most secure VPN servers currently available. More information on the dynamic firewall is available in the security documentation.