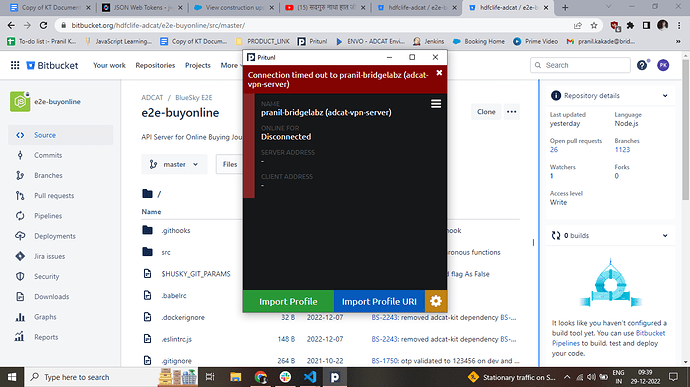
When I Connect my mobile (One Plus 10T - android) hotspot to my laptop (OS - windows 10) … Pritunl will failed to connect … but if connected with my other phone’s hotspot … its working … can anyone please guide me … Pritunl version (v1.3.3373.6)
System Logs =
[2022-12-29 20:33:25][WARN] profile: Failed to sync config
[2022-12-29 20:38:4][WARN] profile: Failed to sync config
[2022-12-29 20:45:20][WARN] profile: Failed to sync config
[2022-12-29 20:46:26][ERROR] AuthError: profile_view: Connection timed out to pranil-bridgelabz (adcat-vpn-server)
[2022-12-29 20:46:47][WARN] profile: Failed to sync config
[2022-12-29 20:47:51][ERROR] AuthError: profile_view: Connection timed out to pranil-bridgelabz (adcat-vpn-server)
[2022-12-29 20:48:27][WARN] profile: Failed to sync config
[2022-12-29 20:49:31][ERROR] AuthError: profile_view: Connection timed out to pranil-bridgelabz (adcat-vpn-server)
[2022-12-29 20:55:6][WARN] profile: Failed to sync config
[2022-12-29 20:56:23][ERROR] AuthError: profile_view: Connection timed out to pranil-bridgelabz (adcat-vpn-server)
[2022-12-29 21:6:44][WARN] profile: Failed to sync config
[2022-12-29 21:7:49][ERROR] AuthError: profile_view: Connection timed out to pranil-bridgelabz (adcat-vpn-server)
Service Logs = 2022-12-30 12:00:53 Server poll timeout, restarting
2022-12-30 12:00:53 SIGUSR1[soft,server_poll] received, process restarting
2022-12-30 12:00:53 Outgoing Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2022-12-30 12:00:53 Incoming Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2022-12-30 12:00:53 TCP/UDP: Preserving recently used remote address: [AF_INET]13.127.231.152:18664
2022-12-30 12:00:53 UDP link local: (not bound)
2022-12-30 12:00:53 UDP link remote: [AF_INET]13.127.231.152:18664
2022-12-30 12:00:57 Server poll timeout, restarting
2022-12-30 12:00:57 SIGUSR1[soft,server_poll] received, process restarting
2022-12-30 12:00:57 Outgoing Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2022-12-30 12:00:57 Incoming Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication
2022-12-30 12:00:57 TCP/UDP: Preserving recently used remote address: [AF_INET]13.127.231.152:18664
2022-12-30 12:00:57 UDP link local: (not bound)
2022-12-30 12:00:57 UDP link remote: [AF_INET]13.127.231.152:18664
2022-12-30 12:00:59 SIGTERM[hard,] received, process exiting
2022-12-30 12:01:12 WARNING: Compression for receiving enabled. Compression has been used in the past to break encryption. Sent packets are not compressed unless “allow-compression yes” is also set.
2022-12-30 12:01:12 DEPRECATED OPTION: --cipher set to ‘AES-128-CBC’ but missing in --data-ciphers (AES-256-GCM:AES-128-GCM). Future OpenVPN version will ignore --cipher for cipher negotiations. Add ‘AES-128-CBC’ to --data-ciphers or change --cipher ‘AES-128-CBC’ to --data-ciphers-fallback ‘AES-128-CBC’ to silence this warning.
2022-12-30 12:01:12 OpenVPN 2.5.6 Windows-MSVC [SSL (OpenSSL)] [LZO] [LZ4] [PKCS11] [AEAD] built on Mar 16 2022
2022-12-30 12:01:12 Windows version 10.0 (Windows 10 or greater) 64bit
2022-12-30 12:01:12 library versions: OpenSSL 1.1.1n 15 Mar 2022, LZO 2.10
2022-12-30 12:01:12 Outgoing Control Channel Authentication: Using 160 bit message hash ‘SHA1’ for HMAC authentication