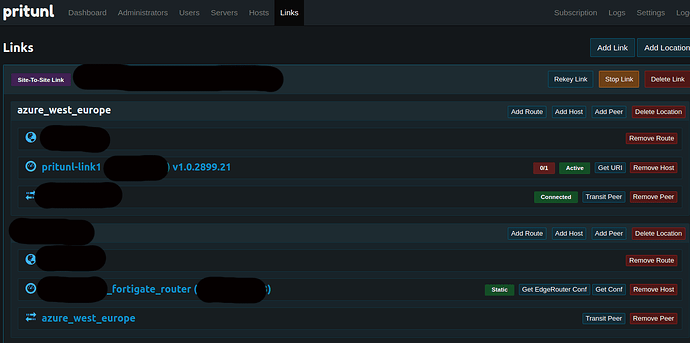
We are trying to setup a site-to-site link between a vpn server running on pritunl and our office network.
A link has been configured on pritunl-server webUI with two locations:
- VM with pritunl-link on Azure cloud:
- We have added the pritunl-link1 host to pritunl-link with
pritunl-link add pritunl://token:secret@test.pritunl.com. - This made the link “Active” on the webUI.
- We have added the pritunl-link1 host to pritunl-link with
- office router (fortigate 60F):
- We got the configuration from the webUI and configured a VPN connection on the router.
- The conenction reports green on the router’s interface.
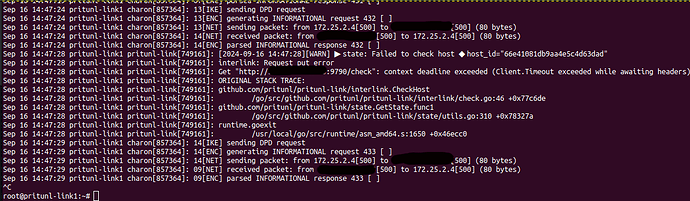
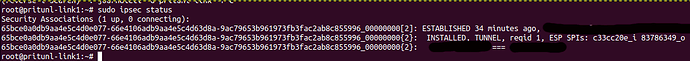
Looking at the pritunl-link journactl we can see that:
-
the ipsec link is established.
-
pritunl-link is throwing an error about the check on port 9790.
The firewall on Azure and on the Fortigate router has been configured to allow all traffic.
But the connection doesn’t work.
I don’t see any other option on the Fortigate router that has anything to do with port 9790.
Before, we had a working link with an Edge Router, which worked fine.
Can you please advise on what might be the problem?